So after some work on it here’s the solution to enable it. I found a few posts on line but they didn't seem to be written very clear for a environment with a Certificate Authority(CA) not on a Domain Controller (DC).
I found that all you really have to do is give the DC the correct type of certificate and it will automatically do LDAP over SSL. An important requirement here is that I didn’t want to force connections to use LDAP over SSL but rather just enable it to work if something wants to use it.
Environment
Microsoft Active Directory: Windows 2008
Certificate Authority: Windows 2008 Server that is not a Domain Controller
Solution
Enable The Domain Controller Authentication Certificate Template on the Certificate Authority
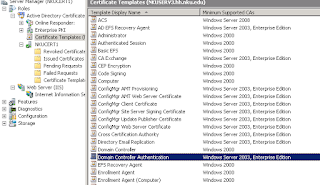
Starting with your Certificate Authority (CA) we need to make sure that the Domain Controllers (DC's) can enroll with the CA in order to obtain the correct Certificates. There is a Certificate Template for this that exists by default. To configure this Logon to the CA and open Server Manager and then expand the roles till you get the view below.
- Expand the tree till you see the Certificate Templates folder and look for the Domain Controller Authentication the default existing template.
- Then expand the CA server and check if its listed under its Certificate Templates folder as well. If the Domain Controller Authentication is listed in both places then it exists and is enabled. If it isn't under the CA's Folder then we need to enable the Domain Controller Authentication Certificate Template.
- Right click Certificate Templates under the CA, Click New, then and Click Certificate Template to Issue. Select the Domain Controller Authentication and then click OK.
Note: If you want to change how long the certificate is valid for or other values. You can edit the template before we enroll the Domain Controllers.
Obtain the "Domain Controller Authentication" Certificate on the Domain Controller
We need to enroll our Domain Controllers with the CA to obtain the new Domain Controller Authentication certificate. This will have to be configured on all of the Domain Controllers. But to start should tested on just one of them before continuing to configure it on all of them
- Login into the Domain Controller you want to test the LDAP over SSL.
- Open a command prompt as an administrator. To open a command prompt as an administrator, click Start. In Start Search, type Command Prompt. At the top of the Start menu, right-click Command Prompt, and then click Run as administrator. If the User Account Control dialog box appears, confirm that the action it displays is what you want, and then click Continue.
- To open Microsoft Management Console (MMC), type mmc, and then press ENTER.
- Click File, click Add/Remove Snap-in, select Certificates from the available snap-ins, and then click Add.
- In the Certificates snap-in, click Computer Account, and then click Next.
- In the Select Computer, click Local Computer, and then click Finish and then OK.
- In the console tree, expand Certificates - Local Computer, expand Personal, and then expand Certificates.
- Note: Trying to do this on a remote computers Cert store didn't work as the options to enroll wasn't there.
- Right Click and choose All Task, Click Request New Certificate. A Before You Begin window will prompt you. Click Next.
- Select Active Directory Enrollment Policy. And Click Next.
- Check Domain Controller and Domain Controller Authentication and click Next.
- In the Certificate Enrollment, a status window should show the Domain controller enrolling and then Status: Succeeded. Click Finish.
Note: On my read only domain controller the enroll failed but I haven't sat down to figure out why yet.
Links
http://technet.microsoft.com/en-us/library/ee411009(WS.10).aspx





great post you made life easy. now i not need any network support..
ReplyDeleteGreat post, thank you. Was having difficulty finding anything that displayed how to do this in a simply way. Just to confirm worked perfect.
ReplyDeleteThanks a lot!!! I knew there was a certificate issue, but like you said there were no good post out there. Your post was very helpful!!! Thanks
ReplyDeleteAwesome post- Thanks for the help!
ReplyDeleteMark
Chris,
ReplyDeleteDoes the CA have to be an enterprise CA or can it be stand alone?
Anthony
This comment has been removed by the author.
ReplyDeleteOnce I realized the CA needed to updated, I was able to get certificates out of it. The only issue now seems to be that I cannot authenticate no matter what parameters I use for logging in. Any thoughts on the following error?
ReplyDeleteERROR: bind failed: Invalid credentials, 80090308: LdapErr: DSID-0C0903A9, comment: AcceptSecurityContext error, data 52e, v1db0:
I know the creds are good. Using Standard Schema and have tried setting Domain Group to 'Domain Admins', as well as creating a new group specifically for DRAC access.
Thanks! Cheers...
Hello,
ReplyDeleteUnfortunately I get stuck at "Check Domain Controller and Domain Controller Authentication and click Next."
Can you see my stack overflow question* about this?
*http://stackoverflow.com/questions/8002950/how-to-obtain-the-domain-controller-authentication-certificate-on-the-domain-c
Your pictures are out of order for Windows Server 2008 R2. The select server enrollment policy is before the request certificates, within the certificate enrollment section. Thanks for the tutorial.
ReplyDeleteperfect.. Thanks a lot for yout work
ReplyDeleteJust what I was looking for thanks for your efforts.
ReplyDeletegreat post! thank you!
ReplyDeleteExcellent post
ReplyDeleteThanks for this Chris, I've been searching for this information and found some bizarre suggestions; 10-page how-tos, dozens of certutil and certreq command permutations, vbs scripts that generate 8 intermediate files, etc. I kept thinking man, it can't really be this difficult. You nailed it. Thanks.
ReplyDeleteI followed this tutorial, however port 636 isn't being listened on. ldp.exe will connect on 389 w/o ssl, but not on 636 w/ ssl. Any ideas?
DeleteI followed this tutorial and now our backup software will work with ldap over ssl. Oddly the ldp tool still fails to connect on 636. The problem is now that we can't map to a webdav drive on another server, keep getting an error about "Mutual Authentication failed, the server's password is out of date at the Domain Controller." I've tried clearing the SSL state in Internet options. I'm not an expert in this area, just wondered in anyone had any ideas? Thanks, Stephen
ReplyDeleteFollowed these instructions to a "T". I second Erik. 636 isn't being listened on. How to get AD to listen on 636???
ReplyDeleteAt least someone's in the same boat as me. Find anything that works?
Deleteonce i open the mmc and add certificates snapin and browse my local computer. I see "personal" but no subfolder of "Certificates". how do i view that subfolder "certificates" under personal?
ReplyDeleteMe too, but did you ever get a response?
DeleteIve been looking everywhere for this, as you say there are lots of articles that are not concerned with DCs
ReplyDeleteThanks very much
For the comments related to LDP on port 636, I believe you may need to publish the Root CA certificate and also the CRL (Certificate Revocation List) to AD.
ReplyDeleteIt really depends on how you have your PKI infrastructure configured. I've setup PKIs according to the following documentation and have no issue connecting to a DC on 636 with LDP.
http://marckean.wordpress.com/2010/07/28/build-an-offline-root-ca-with-a-subordinate-ca/
Really useful post. I am struggling a bit though however.
ReplyDeleteMy setup is Server 2008 SP2 (not R2) Standard. The Server is a Domain controller which I already use for NPS and Radius and has the Active Directory Certificate Services role setup.
My problem is that when I try and enable the Domain Controller Authentication Template on the CA, when I go New - Certificate Template to Issue, the Domain Controller Authentication template is not in the list of certificate templates (Along with others that are missing). This problem was also mentioned here so I ran the command certutil -SetCAtemplates +domaincontrollerauthentication which works. The problem I then have is that when I try and enrol the certificate to one of my Domain Controllers (mmc - Certificates (Computer Account) - Personal - Root), when I select Request New Certificate and select Domain Controller Authentication and hit Enrol, I get "The requested certificate template is not supported buy this CA. The request was for a certificate templates that is not supported by the Active Directory Certificate Services Policy".
I checked permissions on the certificate and "Authenticated users" has read access. I have read certain certificate restrictions for Server 2008 Standard but not sure if this applies to what I am trying to achieve.
Can anyone point me in the right direction for this?
Hi, I would like how to do to renew a Domain controller certificate for a Core server-based domain controller ??? because I cannot use the MMC Certificates from a Core server. I guess I need to use CERTUTIL, but how can I do to request such certificates against an W2k8R2 ADCS based enterprise pki (running on dedicated servers not DCs) ?
ReplyDeleteThanks for the solution! Why can't Microsoft just publish something as simple as this to get it working. I've been searching for days trying to figure this out and turns out all we were missing was the certificate with the "Domain Controller Authentication" on each DC. Everything else was there automatically when we set up the CA server.
ReplyDeleteOn a side note, if you have multiple forests (we do), you'll only get the root cert for your own forest by default, and LDAPS connections to another forest will not succeed until you add the root cert from the CA server in that forest to the client Trusted Root Certificates.
Took a little bit to figure that one out, as obvious as it is.
Thanks Chris, this article saved my bacon
ReplyDeletewhen I click on
ReplyDeleteNew --> certificate template to issue --> the enable certificates template appears however I do not see Domain Controller Authentication as an option. I do see Domain Controller Authentication when I have Certificate Templates selected in the left pane.
Why do I not see it when I click Certificate template to issue?
Ever seen LDAPS Implementation where login to Application is delayed by up to 1 minute. Certs are verified. Working on a Service Now Integration where LDAP works fine but LDAPS is hanging.
ReplyDeleteTrying to troubleshoot an authentication issue. This post helped me to quickly verify my configuration at the DCs and saved me a lot of time in research. Thank you!
ReplyDeleteCool to know that once you have the right certificate, everything is much less of a problem. I think that people who are new to using SSL on their site will find a lot of issues pop up every now and then. However, helpful advice can help them get over those challenges quickly.
ReplyDelete